Bitcoin mining Yahoo
A few days ago it was revealed that numerous European users of Yahoo, as many as two million, had gotten infected with malware from virus-laden ads served by Yahoo's homepage during the period from December 31 to January 3. The company admitted as much when it revealed that "From December 31 to January 3 on our European sites, we served some advertisements that did not meet our editorial guidelines – specifically, they spread malware." Users in North America, Asia Pacific and Latin America weren't affected, Yahoo said. Nor were users of Apple Macs or mobile devices. "We will continue to monitor and block any advertisements being used for this activity, " the company added. "We will post more information for our users shortly." What was not clear is just what function the ad virus served.
According to the Guardian, "some of the malware would turn PCs into bitcoin miners - a huge drain on its computing resources - without users' knowledge. Yahoo has been criticised for not saying how many people could be affected or doing anything to help those with the malware, which attacked flaws in Java modules on systems."
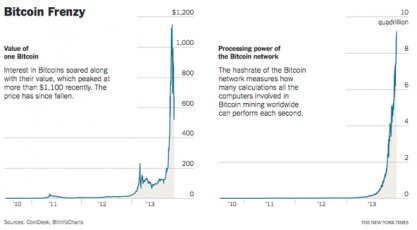
As a reminder, in "A trip through the Bitcoin mines" we showed just how extensive the capital requirements can be for any legitimate Bitcoin mining operation, where the distributed calculations used to extract new Bitcoins have now risen to a stunning 10 quadrillion per second.
So what is an enterprising hacker in need of some quick cash, but unwilling to spend the CapEx for procuring the expensive equipment (especially when buybacks and dividends are so much more attractive, just kidding) to do? Why force others to do the mining for them. This is precisely what the creator of the Yahoo-hosted virus did.
According to Light Cyber, a security research firm which warned Yahoo of the attacks in late December, one of the malware programs delivered in the attack turned the victim's computer into a bitcoin miner. The computer is set to work performing the calculations required to make the bitcoin network run, but the rewards for doing so accrue to the malware writer.